To build up a library is to create a life. It’s never just a random collection of books.
Z-Library
1
Follow this link or find "@BotFather" bot on Telegram
2
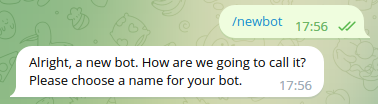
Send /newbot command
3
Specify a name for your chatbot
4
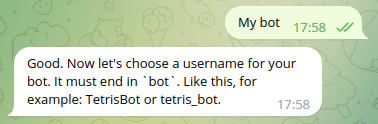
Choose a username for the bot
5
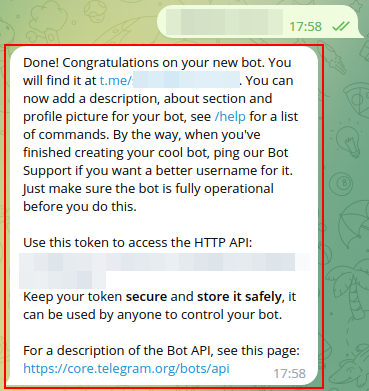
Copy an entire last message from BotFather and paste it here